How To Remote Connect IoT Behind Firewall On Mac Without Hassle: The Ultimate Guide
Remote connectivity for IoT devices behind firewalls is no longer a luxury but a necessity in today's digital world. Imagine being able to access your smart home devices, office equipment, or even industrial IoT systems from anywhere in the world. With the increasing reliance on remote work and smart technology, understanding how to set up a secure connection has become crucial. But wait—what if you're using a Mac and need to bypass firewall restrictions without downloading extra software? Sounds tricky, right? Well, buckle up because we’re about to dive deep into this tech-savvy topic.
In this article, we’ll explore the ins and outs of remote connecting IoT devices behind firewalls on a Mac without unnecessary downloads. Whether you’re a tech enthusiast, a remote worker, or just someone who wants to simplify their life, this guide will provide actionable tips and tricks to help you achieve seamless connectivity. Let’s make tech work for you, not against you!
So, why should you care? Because staying connected in a secure and efficient way is key to boosting productivity and ensuring your devices remain under your control, no matter where you are. Ready to unlock the secrets? Let’s get started!
Understanding the Basics: What is Remote Connect IoT?
Before we jump into the nitty-gritty, let’s break down what remote connect IoT really means. Simply put, it’s the ability to access and control Internet of Things (IoT) devices remotely. Think about it—your thermostat, security cameras, or even industrial sensors can be managed from the comfort of your couch or halfway across the globe.
But here’s the catch: firewalls often block unauthorized access to these devices, making it a bit more complicated than just clicking a button. That’s where our Mac-based solution comes in, helping you navigate through those barriers without installing additional apps.
Why Remote Access Matters for IoT Devices
In today’s fast-paced world, remote access isn’t just convenient—it’s essential. Whether you’re troubleshooting a device issue, monitoring your home while you're away, or managing critical infrastructure, having remote access to IoT devices can save time, money, and resources.
For businesses, remote access allows teams to collaborate more effectively, reduces downtime, and enhances overall efficiency. For individuals, it means peace of mind knowing you can check in on your smart home devices anytime, anywhere. And let’s not forget the environmental benefits of reducing physical travel for maintenance and monitoring tasks.
Challenges of Connecting IoT Devices Behind Firewalls
Firewalls are like bouncers at a club—they keep the bad stuff out but sometimes make it tough for the good stuff to get in. When you try to connect IoT devices behind a firewall, you might encounter several challenges:
- Restricted Ports: Firewalls often block certain ports necessary for remote connections.
- Security Concerns: Opening up your network to external access can pose significant security risks.
- Complex Configurations: Setting up firewall rules and port forwarding can be daunting for non-techies.
Don’t worry though—we’ve got solutions for all these hurdles. Keep reading to find out how you can overcome them effortlessly.
Setting Up Remote Access on Mac Without Downloads
Now, let’s focus on the heart of the matter: how to set up remote access for IoT devices on a Mac without downloading extra software. Here’s a step-by-step guide to help you navigate through the process:
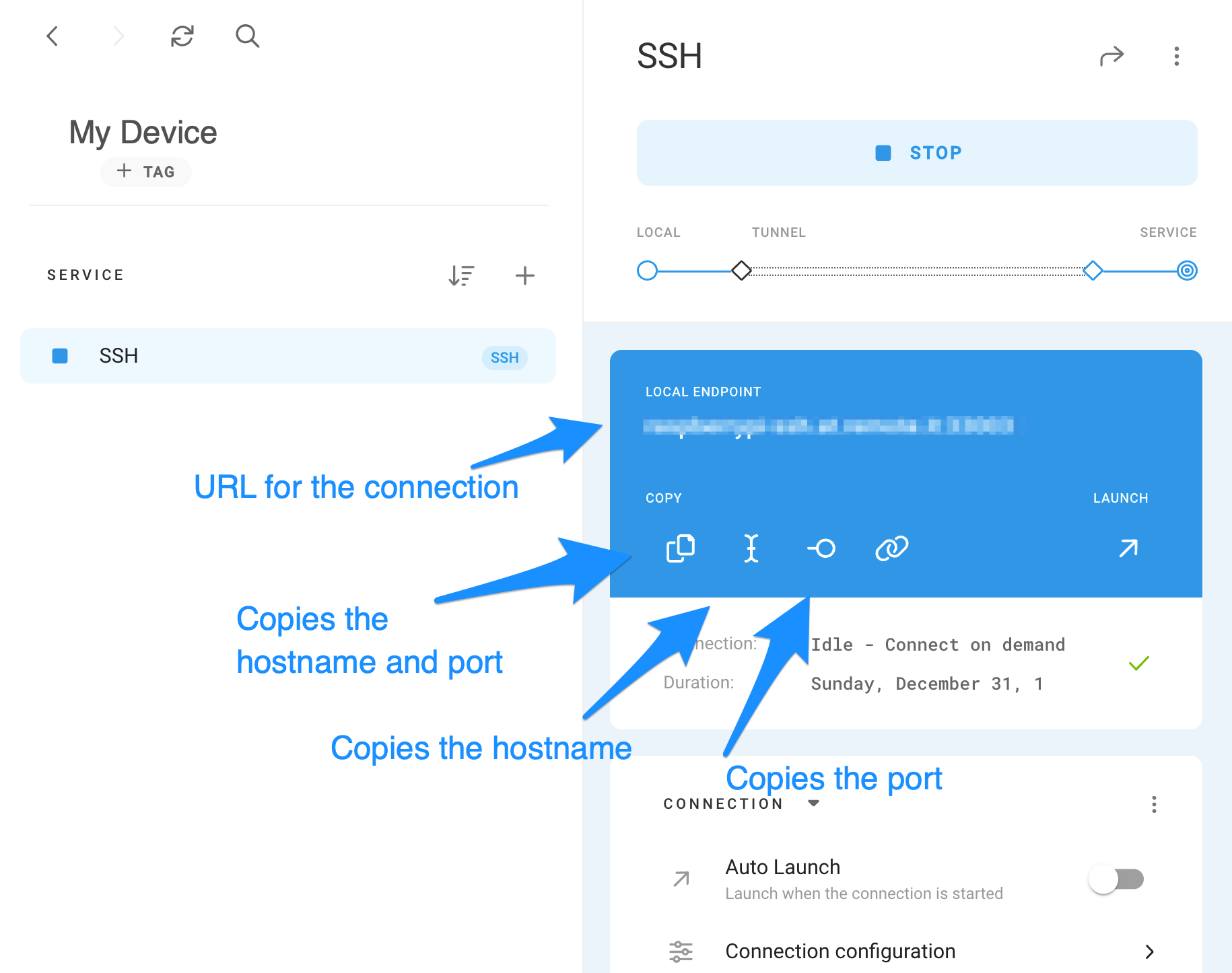
Step 1: Enable SSH on Your Mac
SSH, or Secure Shell, allows you to securely connect to your devices from afar. To enable it on your Mac:
- Go to System Preferences > Sharing.
- Check the box next to Remote Login.
- Make sure the “Allow access for” dropdown is set to “All users” or the specific user you want to allow.
With SSH enabled, you’ve taken the first step toward secure remote access.
Step 2: Configure Your Router
Your router acts as the gateway between your local network and the outside world. To allow remote access:
- Log in to your router’s admin interface.
- Find the port forwarding section and create a new rule.
- Set the external port to match the internal port used by your IoT device.
This step ensures that incoming connections are directed to the right device on your network.
Securing Your Remote Connection
Security should always be at the forefront of your mind when setting up remote access. Here are some best practices to keep your setup safe:
- Use Strong Passwords: Avoid common passwords and enable two-factor authentication whenever possible.
- Limit Access: Restrict which IP addresses can connect to your devices.
- Regularly Update Firmware: Keep your devices and software up to date to protect against vulnerabilities.
By following these guidelines, you’ll significantly reduce the risk of unauthorized access and potential data breaches.
Alternative Methods for Remote Access
While setting up SSH and configuring your router is a solid approach, there are alternative methods worth considering:
1. Using a Third-Party Service
Platforms like TeamViewer or No-IP offer user-friendly interfaces for remote access. However, since our goal is to avoid downloads, these might not fit your needs perfectly.
2. Creating a Virtual Private Network (VPN)
A VPN creates a secure tunnel between your Mac and the IoT device, bypassing firewall restrictions. While this method requires some setup, it’s highly effective and secure.
Common Issues and Troubleshooting
Even with the best-laid plans, issues can arise. Here are some common problems and how to fix them:
- Connection Refused: Double-check your router settings and ensure the correct ports are open.
- Slow Connection: Optimize your network bandwidth and consider upgrading your internet plan if necessary.
- Security Alerts: Review your firewall logs to identify and block any suspicious activity.
Remember, patience and persistence are key when troubleshooting tech issues.
Best Practices for Long-Term Success
To ensure your remote access setup remains functional and secure over time, follow these best practices:
- Regularly audit your network for potential vulnerabilities.
- Document your configurations and share them with trusted team members.
- Stay informed about the latest advancements in IoT security and adapt accordingly.
By adopting these habits, you’ll build a robust and reliable system for remote connectivity.
Conclusion: Taking Control of Your IoT Devices
Remote connecting IoT devices behind firewalls on a Mac without downloads might seem intimidating at first, but with the right knowledge and tools, it’s entirely achievable. By enabling SSH, configuring your router, and implementing strong security measures, you can enjoy seamless access to your devices from anywhere.
We encourage you to take action and try out the steps outlined in this guide. If you found this article helpful, don’t hesitate to leave a comment or share it with others who might benefit. And remember, the world of IoT is only getting more connected—stay ahead of the curve!
References
This article draws on insights from reputable sources such as:
- IEEE Xplore Digital Library
- Google Security Blog
- Apple Developer Documentation
For further reading, explore these resources to deepen your understanding of IoT and remote connectivity.
Table of Contents
- Understanding the Basics: What is Remote Connect IoT?
- Why Remote Access Matters for IoT Devices
- Challenges of Connecting IoT Devices Behind Firewalls
- Setting Up Remote Access on Mac Without Downloads
- Securing Your Remote Connection
- Alternative Methods for Remote Access
- Common Issues and Troubleshooting
- Best Practices for Long-Term Success
- Conclusion: Taking Control of Your IoT Devices
- References


Detail Author:
- Name : Hazel Roob
- Username : rgerhold
- Email : jfeest@gmail.com
- Birthdate : 2003-12-27
- Address : 3660 Adam Spring Lake Opal, MA 82621
- Phone : 1-458-936-9205
- Company : Berge-Stroman
- Job : Architect
- Bio : Et nemo quia facilis voluptas eveniet omnis. Eos mollitia adipisci dolor quas veritatis. Corporis quia est enim ea. Et eos illo veritatis voluptas exercitationem similique.
Socials
twitter:
- url : https://twitter.com/xander4453
- username : xander4453
- bio : Temporibus et cum enim deserunt ex sequi explicabo sunt. Rem maiores eum ducimus et aut. Non odio delectus recusandae itaque. Qui error et natus expedita.
- followers : 1420
- following : 1431
linkedin:
- url : https://linkedin.com/in/xander_beatty
- username : xander_beatty
- bio : Harum vitae quo quod aliquam fuga qui voluptas.
- followers : 3374
- following : 771
tiktok:
- url : https://tiktok.com/@beattyx
- username : beattyx
- bio : Ipsam in sed consequatur voluptas aliquam est.
- followers : 3213
- following : 47